Hello Everyone,
I wanted to share this story NBC News did on a new type of scam going on out there, with the holiday season nearing you need be aware of internet crooks trying to steal your info on the web. Please read this article so you can be aware of the new scam that is out there, and be safe!
malware
CryptoLocker crooks launch new 'customer service' website for victims
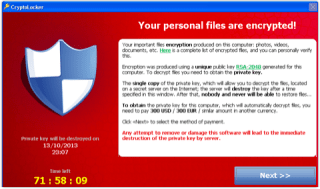
It’s the latest twist in the global CryptoLocker ransomware attack. This diabolically nasty malware locks up all of the victim’s personal files — and in some cases, backup files, too — with state-of-the-art encryption. The bad guys have the only decryption key and they demand $300 or two Bitcoins to get it.
“It’s been a disaster for many of the people hit with it,” said Lawrence Abrams who has been tracking the spread of this infection on BleepingComputer.com
Within the past few days, the criminal gang behind CryptoLocker created a site for victims who need help making their required extortion payments.
“These guys have some big cojones,” said security expert Brian Krebs, who writes the blog KrebsOnSecurity.
The CryptoLocker Decryption Service allows victims to check the status of their “order” (the ransom payment) and complete the transaction. I am not making this up!
Those who paid the ransom (with either Green Dot cards or Bitcoins), but did not get the decryption key — or got one that didn’t work — can download it again.
Those who missed the 72-hour deadline can also get their key, but the price jumps from two Bitcoins to 10. At today’s market value, that’s nearly $4,000. And Green Dot is not accepted with this extended-deadline service.
Why are the CryptoLocker crooks doing this?
“They were leaving money on the table,” Abrams told me. “They created this site to capture all of the money they were losing because people couldn’t figure out how to make the ransom payment or missed the deadline.”
The bad guys also ran into some technical problems after they launched their attack. It turns out that when antivirus software removes CryptoLocker from an infected computer, the victim can no longer pay the ransom and decrypt their files. To do that, they had to re-install the CryptoLocker malware, something that was not only weird, but cumbersome.
By using the customer service site, victims can get a key that will unscramble their files without the need to re-infect their computers.
Is this the new reality?
Law enforcement and cyber security experts always advise victims of ransomware attacks not to pay the ransom. After all, that extortion money goes to fund a criminal operation, and there’s no guarantee the files will be released.
But when you’re the victim, when all of your data has been encrypted and you don’t have a suitable backup, you’re faced with two choices: pay up or have those files frozen forever. That’s why so many people are paying and why security experts fear more of this nasty malware is on the way.
“Anytime you see an underground business that is doing well, you will always see more people copying it,” said Krebs. “Unfortunately, I think these destructive attacks are here to stay and they’re only going to get worse and more intense.”
Sean Sullivan, security advisor at F-Secure, agrees.
Until now, ransomware attacks have been limited by the lack of a global payment method. It took a lot of work to get paid in different parts of the world. Bitcoin, the new digital currency, solves that problem.
“CryptoLocker, using Bitcoin, might finally have reduced the overhead of not having a global form of payment,” Sullivan said. “We’re getting to the tipping point where ransomware will become epidemic because it’s not that hard to get paid anymore.”
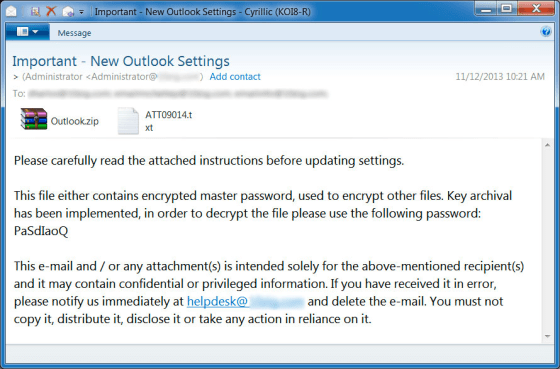
There are various ways for malware to infect your computer. Security experts tell me CryptoLocker is delivered in a Zip file attachment. Open that attachment and the malware is loaded onto your machine.
Some antivirus software can now detect CryptoLocker hidden in a Zip file and prevent the infection. So, a couple of days ago, the bad guys modified their attack.
According to Lawrence Abrams at Bleeping Computer, the Zip files containing CryptoLocker are now password protected. That little trick gets them past the security software.
Abrams said it appears the password “PaSdIaoQ” is the same for everyone. Open that attachment and your files are toast.
How do you protect yourself?
It’s the same advice you’re heard before: Don’t open attachments from an unknown sender, have up-to-date security software and back-up your files religiously. And because CryptoLocker can compromise files already backed-up, you need to reassess how you do your backups.
Network drives (whether physical or in the cloud) that are always connected to your computer are often vulnerable. Krebs suggests doing a manual backup and then disconnecting the drive when you’re done. It’s a lot more work, but much safer.
Krebs warns that we are now dealing with a new generation of malware. Once it’s done its damage, you cannot undo it yourself.
“This is scary stuff,” he said. “People need to rethink how they protect their important files.”
In a new article on his blog, Krebs recommends two tools that can block CryptoLocker infections: CryptoPrevent from Foolish IT for individual windows users and the CryptoLocker Prevention Kit from Third Tier for small business administrators.
Till next time!
Much Success!
Keith A. Holloman CEO/Founder
Keith@ubuildyourwebsite.com
U Build Your Website Web Hosting Services
Specializing in Websites Start-Ups "Connect to the World!"


















Your article is really informative and content rich, not only is it reader friendly but easy to understand as well. Please visit vma website design if ever you need options.
ReplyDelete